|
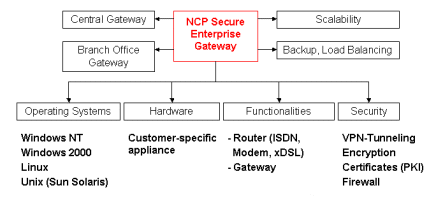
NCP Secure Enterprise Servers represent the central
components for the Secure Enterprise Clients. They supply the platform for
"star-type" access to the corporate network from distributed standalone
PCs and branch office networks. Primarily, this places the highest demands
on server software performance in larger remote access projects involving
several thousand users. The router, bridge, and gateway functionalities
that are implemented enable the following operating modes:
- Direct on the public network (ISDN) as Network Access Server
(NAS) / router
- In the LAN as gateway, e.g. behind an existing IP router in
the corporate headquarters, or a branch office, as other side for
Secure Enterprise VPN and VPN/PKI Client).
NCP Secure Enterprise
Servers allow dial-in connections, as well as dial-out connections.
Integrated firewall mechanisms (port filters) ensure reliable protection
against unauthorized access. As central components, NCP Secure Enterprise
Servers organize and monitor all data streams to and from de-centralized
organizational units (teleworkstations and PC networks). Configuration is
conveniently handled via the Secure Server Manager (included in the
standard scope of delivery).
The software is modular and highly
scalable. Thus small, medium-size, and large projects can be handled with
one and the same software - simply through upgrades. This also applies for
migration to a higher security level. Any PC-based system can be used as
hardware. Its capacity will determine the performance of the entire remote
access solution.
Various NCP software clients:
- NCP Secure Enterprise VPN Gateway und
- NCP Secure Enterprise VPN/PKI Gateway.
The most important delimiting criteria are the supported security features of the NCP Security Management, Encryption and firewalling, (Standard Security), VPN tunneling (Advanced Security), as well as certificates (Strong Security).
All product variants come standard with router functionalities and they can be directly connected to the public network if necessary. For ISDN, the Basic Rate Interface (BRI) as well as the Primary Rate Interface (PRI) are supported. For security reasons (RFC 2888), the VPN and VPN/PKI Gateway(s) should be installed behind the Network Access Server (NAS) and the firewall, in the secure Demilitarized Zone (DMZ). The tunnels end in the gateway, behind the firewall, without public IP address, i.e. the system is not "visible" from the Internet (Reverse Port Mapping). All that is required in the firewall is opening a single UDP port.
Enterprise High Availability Services ensure failsafe security and load balancing, if multiple VPN gateways are operated in parallel.
In conjunction with the corresponding NCP client, the Secure Enterprise VPN/PKI-Gateway offers the highest level of security currently available for remote data transmission, or for remote access applications. The Strong Security Level supports all security technologies required for secure data transmission (data security), as well as shielding the remote systems and the corporate network (access security and network security). The VPN/PKI Gateway represents the central tunnel end-point to the de-centralized client in the Virtual Private Network, on the basis of the end-to-end principle.
Whether or not the teleworker is granted access to the corporate network is decided in a Public Key Infrastructure (PKI) after the certificate check. In this process, the Secure Enterprise VPN/PKI Gateway checks the validity of the user certificate (or server certificate in the case of a branch office gateway) at each connection.
This can be accomplished in one of two ways:
- Online, this means that certificates will be checked for a block notice, online via OCSP (Online Certificate Status Protocol) at the CA (Certification Authority).
- Offline, this means that the CRL (Certificate Revocation List) is downloaded to the VPN gateway at defined intervals and updated.
Each connection attempted with a blocked certificate will be broken off. Client software and server software monitor the validity of a certificate. The system administrator initiates a certificate extension or block via the Secure Enterprise PKI-Manager, as needed.
The Secure Enterprise VPN-Gateway is used in those remote access projects that do not require strong authentication via certificates. In this case authentication is executed in the usual manner, by entering user ID and password. All data are encrypted for transmission in an end-to-end tunnel between the Secure Gateway and the Secure Enterprise VPN Client on the basis of the Advanced Security Mechanisms.
All NCP Secure Gateways have routing functions, and they can be directly operated in the network WAN adapters that must be installed in addition; this enables dial-out and direct dial-in.
|
| | | | | |